Overview
This article describes in detail how to interpret the results you receive back from running a Manual/Interactive scan.
Introduction
The Scan Results Overview and Scan Results Details sections in the Scan tab are designed to facilitate the result analysis process as much as possible. Use the information in the following sections to learn how scan results are interpreted and to know which areas require your immediate attention.
Description
Viewing Scan Results
From the LanGuard console Scan tab, you can view results generated by Manual scans or results stored in the backend database/loaded from a file. Alternatively, you can also launch new manual scans from this location.
To view scan results:
- Launch GFI LanGuard and click the Scan tab.
- Launch a new scan or load the result from the database/XML file.
- Once completed, the results are displayed in the Scan Result Overview and the Scan Results Details sections.
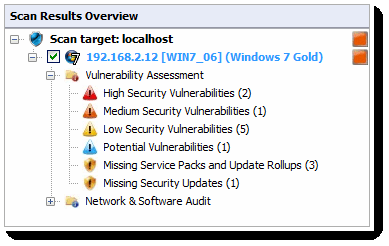
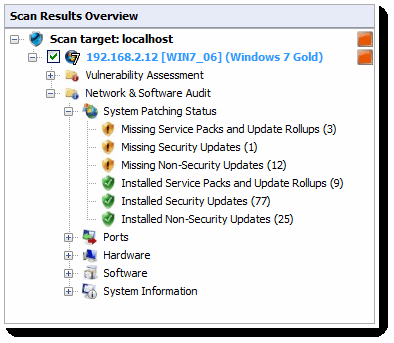
From Scan Results Overview, expand a computer node to access results retrieved during the scan. The contents are organized into two sub-nodes - Vulnerability Assessment and Network & Software Audit.
While a scan is in progress, each computer node has an icon that categorizes the response time. The table below describes the different icons used by GFI LanGuard to categorize the response time. The first icon 

|
Category |
Information |
Description |
 |
Fast response | Less than 25 ms |
  |
Medium response | Between 25ms and 100 ms |
  |
Slow response | More than 100 ms |
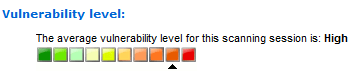
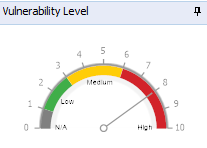
Vulnerability Level Rating
The GFI LanGuard vulnerability level is a rating assigned to each scanned computer. This can be checked from:
-
Scan Results Details – This section in the Scan tab provides you with a vulnerability level meter assigned the computers/groups that have been scanned
-
Dashboard - The Dashboard tab provides you with information for specific computers or selected groups of computers, from the computer tree. Select the computer/group and view the vulnerability meter from the right pane. Select the Entire Network to view the vulnerability level for all your scan targets.
The vulnerability levels are calculated using a weighting system for the various levels of vulnerabilities. High vulnerabilities are worth more points than lower vulnerabilities, on the exact details refer to the article Calculation, Classification, and Meaning of the GFI LanGuard Vulnerability Levels.
Vulnerability Assessment
Vulnerability assessment is one of the scan results sub-nodes from available in the Scan Results Overview. It is further broken down into vulnerability group classifications. Click on any Vulnerability Assessment node to view the security vulnerabilities identified on the target computer grouped by type and severity.
High-Security Vulnerabilities
Click on the High-Security Vulnerabilities for a list of weaknesses discovered while auditing a target device. They are grouped, refer to the table below for the group descriptions:
|
Group |
Description |
| Mail, FTP, RPC, DNS, and Miscellaneous | Shows vulnerabilities found on FTP servers, DNS servers, and SMTP/POP3/IMAP mail servers. Links to Microsoft® Knowledge Base articles or other support documentation are provided. |
| Web | Lists discovered vulnerabilities on web servers (such as wrong configuration issues). Supported web servers include Apache, Internet Information Services (IIS®), and Netscape. |
| Services | Lists vulnerabilities discovered in active services as well as the list of unused accounts that are still active and accessible on scanned targets. |
| Registry | Registry settings of a scanned network device are listed. Links to supporting documentation and short vulnerability descriptions are provided. |
| Software | Enumerates software installed on the scanned network device(s). Links to supporting documentation and short vulnerability descriptions are provided. |
| Rootkit | Enumerates discovered vulnerabilities because of having a rootkit installed on the scanned network device(s). Links to supporting documentation and short vulnerability descriptions are provided. |
Note: Weaknesses discovered are grouped by their nature, so Medium- and Low-Security Vulnerabilities sub-nodes have the same list. Moreover, a group can be missing, or presented in more than one sub-node, based on the findings during the scan.
Potential vulnerabilities
Select Potential Vulnerabilities sub-node to view scan result items classified as possible network weaknesses or indicators of potential threats.
Although not classified as vulnerabilities, such scan result entries still require particular attention.
For example, during vulnerability scanning GFI LanGuard enumerates all modems installed and configured on target computers. If unused, modems are no threat to your network. However, if connected to a telephone line, these modems can be used to gain unauthorized and unmonitored access to the Internet. Users can potentially bypass corporate perimeter security, including firewalls, antivirus, website rating, and web content blocking. This exposes the corporate IT infrastructure to a wide range of threats, including hacker attacks. GFI LanGuard considers installed modems as possible threats and enumerates them in the Potential Vulnerabilities sub-node.
Missing Service Packs
The last two entries in the Vulnerability Assessment subsection are the Missing Service Packs and Update Rollups and Missing Security Updates. As service packs, rollups, and security updates generally resolve vulnerabilities, such as patching 0-day exploits on an application release, they can be found listed under this subsection. For a full list of missing service packs and missing patches that can be identified by GFI LanGuard, refer to the LanGuard reports documentation.
It is also possible to access the relevant bulletin information by right-clicking on the respective service pack and selecting More details>Bulletin Info. For example:
Network and Software Audit
Click Network & Software Audit to view security vulnerabilities identified on scanned targets. In this section, vulnerabilities are grouped by type and severity.
System Patching Status
Click System Patching Status to view all missing and installed patches on a target machine. Available links are:
- Missing Service Packs and Update Rollups
- Missing Security Updates
- Missing Non-Security Updates
- Installed Service Packs and Update Rollups
- Installed Security Updates
- Installed Non-Security Updates.
Note that the Missing Service Packs and Update Rollups and Missing Security Updates are also present here. This is important information and is equally useful for users who may be utilizing one side of the LanGuard vs the other. Some only care about receiving the latest patches, but do not scan for Vulnerabilities. Having these entries in both places ensures that updates and patches won't be missed.
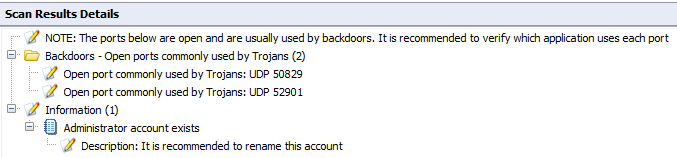
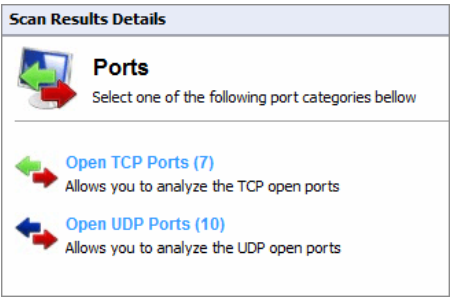
Open Ports
Click Ports to view all open TCP and UDP ports detected during a scan. If a commonly exploited port is discovered to be open, GFI LanGuard marks it in red.
Note: Some software products may use the same ports as known Trojans. For additional security, GFI LanGuard identifies these ports as a threat.
Apart from detecting open ports, GFI LanGuard uses service fingerprint technology to analyze the services that are running behind the detected open ports. With service fingerprint, GFI LanGuard can detect if malicious software is using the detected open port.
Hardware Audit
Click Hardware to view all details discovered by the hardware audit. The hardware audit, amongst others, displays information such as MAC addresses, IP addresses, device type; device vendor, etc. The table below describes the hardware information groups:
| Information |
Description |
|---|---|
| Network Devices | Includes information on all physical, virtual, and software–enumerated devices. |
| Local Drives | Includes information on local drives such as available disk space and file system type. |
| Processors | Includes information regarding the processor of a target machine, such as vendor name and processor speed. |
| Motherboard | Includes information regarding the motherboard of a target machine, such as product name, manufacturer, version, and serial number. |
| Memory details | Includes information regarding the memory allocation of a target machine, such as free physical/virtual memory available. |
| Storage details | Includes information regarding the storage of a target machine, such as floppy disk drive, CD/ROM, and hard drives. |
| Display adapters | Includes information regarding the display and video devices of a target machine, such as the device manufacturer. |
| Other devices | Includes information on devices that do not fall under the mentioned categories above, such as a keyboard, ports, mouse, and human interface devices. |
Software Audit
Click Software to view all details involved in the software audit. The software audit amongst others displays information such as:
- Application name
- Publisher
- Version
The table below describes the hardware information groups:
| Icon |
Description |
|---|---|
| General Applications | Enumerates installed software on scan targets. |
| Antivirus Applications | Lists installed antivirus engines on scan targets. |
| Instant Messenger Applications | Lists all detected instances of Instant messenger applications on scan targets. |
| Patch Management Applications | Lists all the installed patch management applications, detected on your scan targets during a scan. |
| Web Browser Applications | Contains scanned targets that have Internet browsers installed. |
| Firewall Applications | Enumerates information on installed Firewall applications on scan targets. |
| Antiphishing Applications | Lists information on installed antiphishing engines on scan targets. |
| VPN Client Applications | Includes information on installed Virtual Private Network clients on scan targets. |
| Peer–To–Peer Applications | Shows installed Peer–To–Peer applications on scan targets. |
System Information
Click System Information to view all details related to the operating system installed on a target machine. The table below describes the system information groups:
| Category |
Information |
Identify |
|---|---|---|
| Shares |
|
|
| Password Policy |
|
|
| Security Audit Policy |
|
Note: To view the Security Audit Policy, enable auditing on target computers. |
| Registry |
|
|
| NETBIOS names |
|
|
| Groups |
|
|
| Users |
|
|
| Logged On Users |
|
|
| Sessions |
|
|
| Services |
|
|
| Processes |
|
|
| Remote TOD (time of day) |
|
|


Priyanka Bhotika
Comments